Global Windows BSOD Incident (CrowdStrike)
Incident Report
The Incident Overview
On July 19, 2024, at 04:09 UTC, a routine content configuration update pushed by CrowdStrike to its Falcon sensors caused a catastrophic failure in Windows systems worldwide. Within minutes, airlines, banks, emergency services, and media broadcasters experienced the dreaded Blue Screen of Death (BSOD), displaying the error code PAGE_FAULT_IN_NONPAGED_AREA.
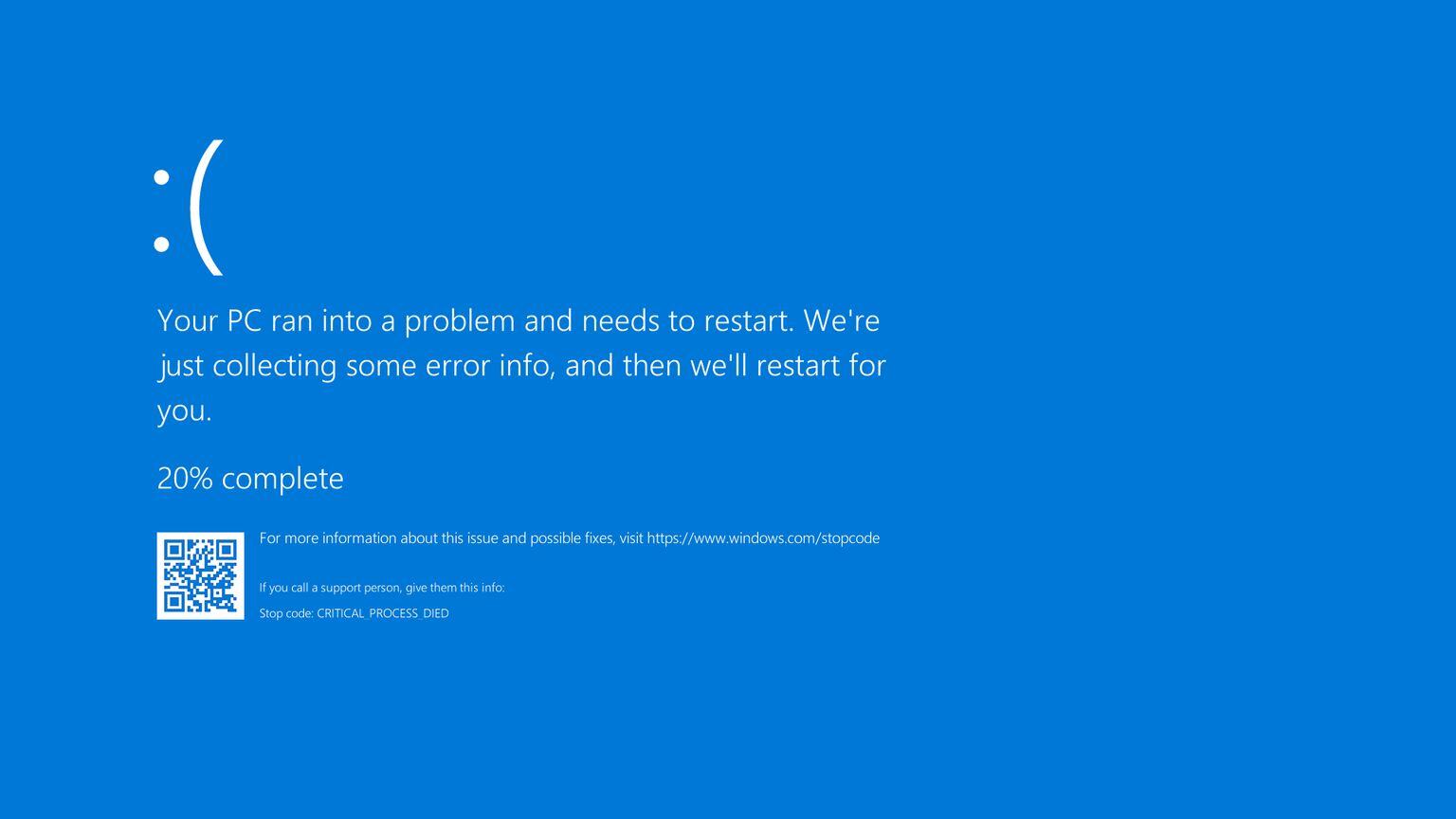
Unlike a typical software bug in an application (Ring 3), this failure occurred in Kernel Mode (Ring 0), which is why it instantly brought down the entire operating system. The update was intended to target malicious named pipes used by cyber adversaries, but instead, it triggered a memory violation in the sensor driver.
Technical Deep Dive: Channel File 291
The root cause was traced to a logic error in a specific configuration file known as Channel File 291 (C-00000291*.sys).
- Not a Driver Binary: It is important to note that the file ending in
.syswas not a kernel driver binary itself, but a binary configuration file interpreted by theCSAgent.sysdriver. - Out-of-Bounds Read: The update introduced a new sensor capability. However, the configuration file instructed the driver to read memory from an address that was not allocated or valid.
- Memory Safety Violation: In C++ kernel development, accessing invalid memory results in a bug check to protect data integrity. The operating system halts execution immediately to prevent data corruption.
"The sensor expected 2 input parameters for the validity check, but the logic in the update only provided 1. This mismatch caused the pointer to reference invalid memory."
The Remediation Process
Because the affected machines would crash during the boot process (Boot Loop), they could not stay online long enough to receive a reverted update from the cloud. This forced IT teams globally to perform a manual remediation on millions of endpoints.
The Workaround:
IT Administrators had to boot into Safe Mode or the Windows Recovery Environment (WinPE) and manually delete the corrupted channel file.
# Navigate to the drivers directory cd C:\Windows\System32\drivers\CrowdStrike # Locate and delete the specific channel file del "C-00000291*.sys" # Reboot the system shutdown /r /t 0
Complications with BitLocker:
For organizations using BitLocker disk encryption, this process was significantly slower. Technicians required the unique BitLocker Recovery Key for every single machine to access Safe Mode, turning a 5-minute fix into a logistical nightmare.
Lessons Learned
This incident highlights the extreme fragility of the software supply chain, especially regarding kernel-level access.
- Canary Deployments: Updates, even configuration files, must be rolled out in stages (e.g., 1%, then 10%, then Global) rather than an immediate global push.
- Kernel vs. User Mode: Security vendors should strive to move more logic to User Mode (eBPF on Linux, or similar frameworks on Windows) to prevent system-wide crashes.
For more details, see the Official CrowdStrike PIR.
SYSTEM NOTES
This log entry has been verified and archived. Access restricted to authorized personnel only.